The Transformative Power of Artificial Intelligence in Cloud Security
Explore the evolving role of AI in cloud security, the benefits it brings, and the challenges it helps organizations overcome.
Join the DZone community and get the full member experience.
Join For FreeCloud computing has reshaped how businesses operate, offering unmatched scalability, flexibility, and cost-efficiency. However, as organizations continue to shift critical operations to the cloud, they face escalating cybersecurity challenges. Traditional security systems often struggle to protect complex, interconnected cloud environments from increasingly sophisticated cyberattacks.
Artificial Intelligence (AI) has emerged as the ultimate game-changer in cloud security. By enabling real-time threat detection, predictive analytics, and automated responses, AI is addressing challenges that older systems cannot handle. A report from Cybersecurity Ventures highlights that by 2028, spending on AI in cybersecurity is expected to exceed $60 billion, underscoring its growing importance. This article explores the evolving role of AI in cloud security, the benefits it brings, and the challenges it helps organizations overcome. This article explores how AI is reshaping cloud security, supported by graphs that provide insights into data trends and AI’s impact.
The Current Cloud Security Landscape
The Explosion of Cloud Data
The volume of data generated by cloud environments is growing rapidly. By 2025, global cloud data volumes are expected to exceed 150 zettabytes. This massive growth creates opportunities for cybercriminals, as traditional systems cannot effectively monitor or analyze such vast datasets.
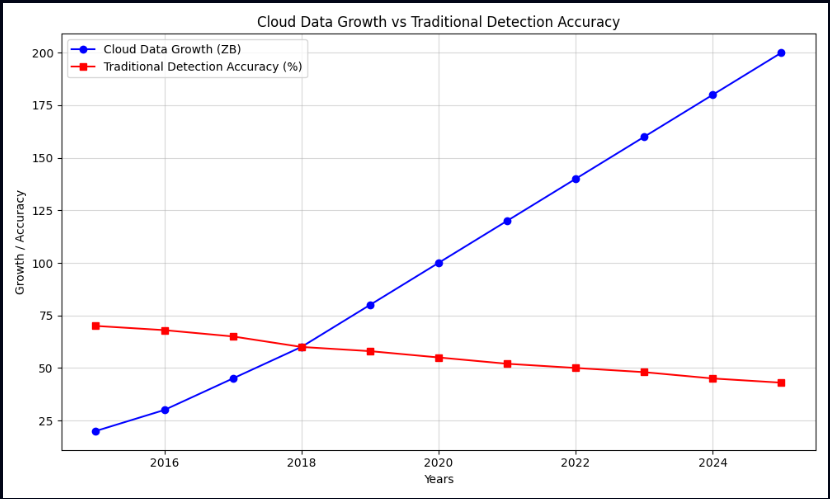
Here’s a graph illustrating how cloud data has grown over time while the accuracy of traditional detection methods has declined:
The above graph shows the exponential growth of cloud data (blue line) alongside the declining effectiveness of traditional security systems (red line). This line graph illustrates how traditional detection systems lose effectiveness as cloud data grows exponentially.
For example, in a large-scale attack in 2022, a global retailer failed to identify unusual data activity in time, resulting in the exposure of millions of customer records. Such incidents highlight the need for smarter, AI-powered systems.
Traditional tools also struggle to detect advanced persistent threats (APTs) or zero-day exploits, which exploit unknown vulnerabilities. This inability leaves critical cloud environments exposed to breaches that can have catastrophic consequences.
AI-Powered Threat Detection and Response
Smarter Threat Analysis
AI systems excel in real-time threat detection by identifying patterns and anomalies in cloud environments. By learning from historical data, AI can distinguish between normal activity and suspicious behavior. For instance, if a user account begins transferring unusually large amounts of data or logging in from an unfamiliar location, AI systems can flag this behavior immediately.
Let’s visualize how AI maintains its accuracy even in complex environments, unlike traditional systems:
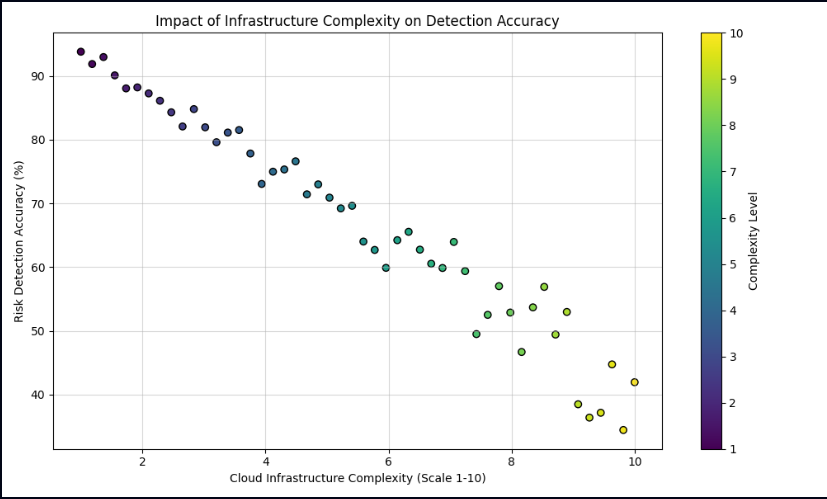
This scatter plot shows that traditional methods lose accuracy as complexity increases, while AI systems maintain higher detection rates.
AI also reduces false alarms. Traditional tools often generate alerts that turn out to be harmless, wasting time and resources. AI minimizes this problem by focusing only on high-risk activities, allowing teams to respond more effectively.
Faster Incident Response
AI doesn’t just detect threats; it can act on them automatically. Automated incident response systems powered by AI can isolate compromised systems, block malicious IP addresses, and revoke access permissions within seconds. This automation significantly reduces the damage caused by attacks like ransomware.
Here’s how AI is enabling security teams to shift their focus from repetitive manual tasks to more strategic work: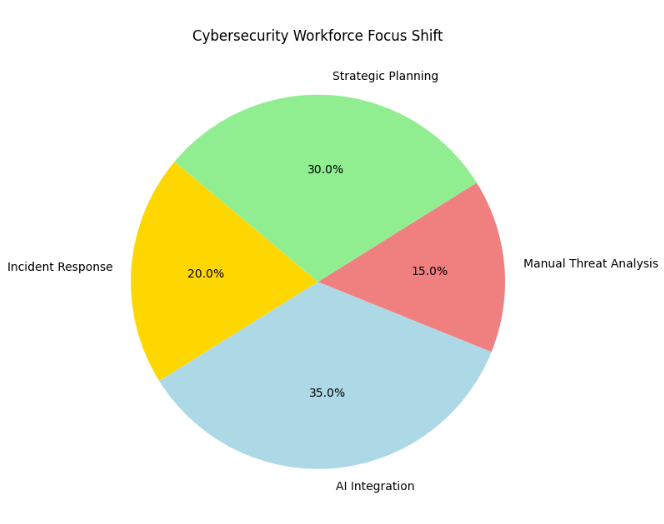
The pie chart above demonstrates how AI reduces time spent on repetitive tasks, allowing teams to prioritize strategic activities like planning and system resilience.
Strategic Implementation of AI in Cloud Security
Optimizing Resources Through AI
AI optimizes resource allocation by prioritizing high-risk incidents and automating routine tasks. Reports indicate that AI-driven automation can reduce cybersecurity costs by up to 20% annually. Sectors like finance, healthcare, and government are investing heavily in AI security tools to protect sensitive data.
Here’s a graph showing investments in AI security by different sectors:
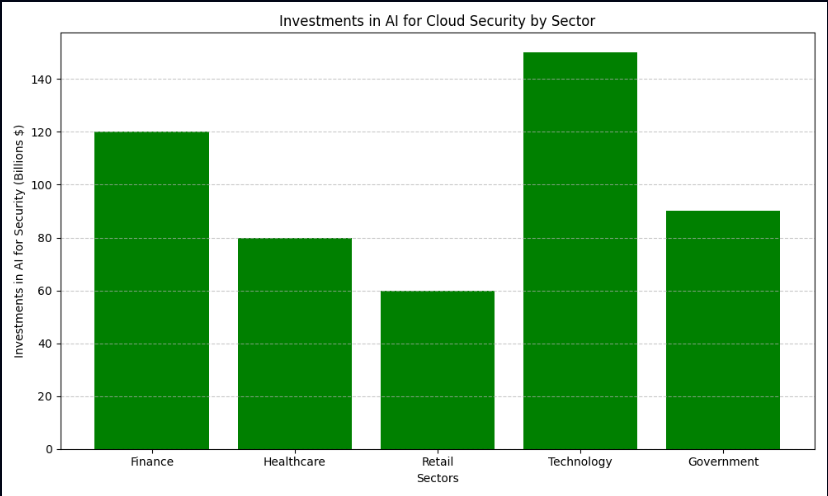
The bar chart above highlights that technology and finance sectors lead in AI investments for cybersecurity.
Emerging Trends and Future Directions
Predictive Analytics: The Next Frontier
AI-powered predictive analytics identifies potential risks before they occur. This helps organizations take preemptive actions, reducing the likelihood of attacks.
Let’s look at the growth of predictive analytics over time:
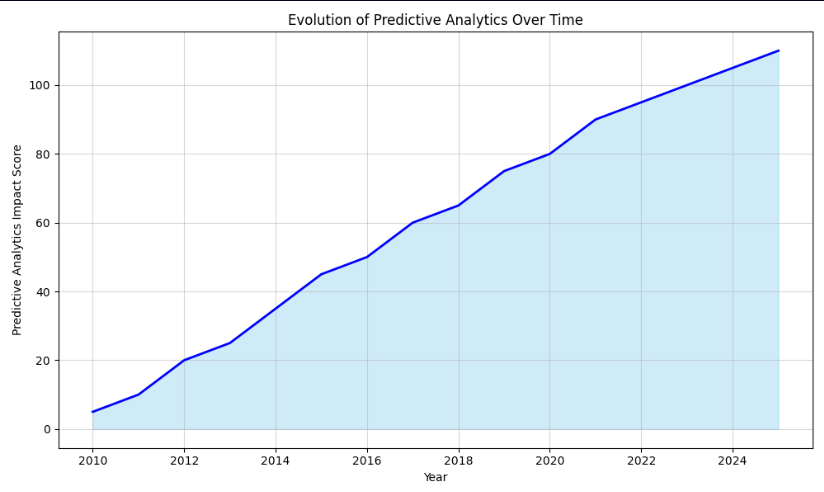
This area chart illustrates how predictive analytics has become a critical part of cloud security, driven by advancements in AI.
Comparing AI with Traditional Security
AI surpasses traditional security systems in scalability, accuracy, and speed. Let’s compare key metrics:
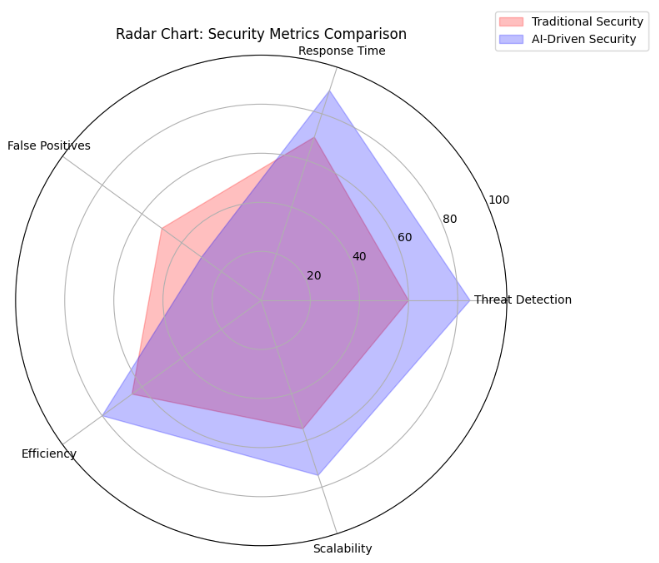
This radar chart compares traditional and AI-driven security systems, showing AI’s superior performance in accuracy, scalability, and speed.
Real-Life Impacts of AI in Cloud Security
AI’s influence is already evident across industries. Educational institutions use AI to protect student data, while hospitals rely on it to secure sensitive patient records. Small businesses, often lacking dedicated security teams, benefit from AI’s automation to achieve enterprise-level protection.
For example, during a phishing attack, AI-based systems have been able to detect suspicious emails within seconds, preventing the attack from spreading across an organization.
Conclusion
AI is changing how we think about cloud security. It can process enormous amounts of data, predict future threats, and act on security breaches instantly. This combination of speed, accuracy, and adaptability makes AI indispensable in defending cloud infrastructures.
As the cloud continues to grow, organizations that embrace AI-driven security will be better equipped to handle evolving threats. By reducing false positives, optimizing resources, and predicting risks, AI ensures that businesses stay safe in an increasingly digital world. The future of cloud security isn’t just reactive—it’s proactive, intelligent, and powered by AI.
Opinions expressed by DZone contributors are their own.

Comments